Enable Access to your accounts using a CloudFormation stack and Control Tower lifecycle events
For comprehensive AWS infrastructure monitoring, Site24x7 needs to automatically discover all instances of various supported services currently running in your account. For this, you need to authenticate and authorize Site24x7 to access your resource. You can achieve this by manually creating IAM user roles or cross-account IAM roles. You can also automatically create an IAM role using a AWS CloudFormation template.
The AWS Control Tower provisions your AWS accounts to meet your organization's security and compliance requirements. Site24x7 uses AWS Control Tower lifecycle events to automatically discover all the accounts in your organization, including new accounts. As a result, you can quickly and easily integrate your AWS accounts with Site24x7.
Use cases
- Consider that you have multiple AWS accounts, which you wish to integrate with Site24x7. Integrating each AWS account can be cumbersome and time-consuming. The AWS Control Tower helps you to set up and manage multiple AWS accounts. You can integrate your AWS accounts with Site24x7 using Control Tower and effectively monitor and manage them in a secure and compliant manner. Using this approach, you can integrate multiple AWS accounts with Site24x7 at the same time.
- The Site24x7-AWS Control Tower integration helps to save time and increase efficiency when managing multiple accounts. For instance, if you create a new account in AWS using Control Tower, the same account gets automatically integrated with Site24x7 without any manual intervention.
Prerequisites
Make sure you have the following before you begin:
- An AWS Management account.
- Accounts Managed using AWS Control Tower.
In addition to the above, ensure that you have the following permissions for the CloudFormation stack to create resources that are required for discovery:
Lambda permissions
Lambda functions are used for communicating with Site24x7, rotating Site24x7 secrets, and for creating stack set instances. The delete permission is used for CloudFormation delete stack operation. The following lambda permissions are used for creating and invoking lambda monitor in the CloudFormation stack:
- lambda:CreateFunction
- lambda:DeleteFunction
- lambda:InvokeFunction
- lambda:GetFunction
- lambda:AddPermission
- lambda:RemovePermission
Secret Manager permissions
Secret Manager is used for storing Site24x7 secrets inside the AWS accounts. These secrets are for communicating with Site24x7 via the Lambda function. The following secret manager permissions are used for creating, rotating and deleting secrets in the CloudFormation stack:
- secretsmanager:CreateSecret
- secretsmanager:DeleteSecret
- secretsmanager:RotateSecret
- secretsmanager:CancelRotateSecret
IAM permissions
The following IAM permissions are used for role creation for Site24x7 integration account and also for giving access to services like Lambda for its function execution:
- iam:CreateRole
- iam:AttachRolePolicy
- iam:PutRolePolicy
- iam:PassRole
- iam:DetachRolePolicy
- iam:DeleteRolePolicy
- iam:GetRole
- iam:DeleteRole
- iam:CreatePolicy
- iam:CreateServiceLinkedRole
KMS permissions
The following permissions are used for the creation and deletion of the KMS key by the CloudFormation service. This key will be used by Secret Manager for encryption and decryption purposes.
- kms:Decrypt
- kms:PutKeyPolicy
- kms:TagResource
- kms:Encrypt
- kms:ScheduleKeyDeletion
- kms:DescribeKey
- kms:CreateKey
- kms:EnableKeyRotation
- kms:UpdateAlias
- kms:GenerateDataKey
- kms:CreateAlias
- kms:DeleteAlias
Eventbridge permissions
The following permissions are used for creating a rule for the Control Tower Create Account event, to trigger the Site24x7 Lambda function to send those details to Site24x7 for new account creation.
- events:PutRule
- events:RemoveTargets
- events:DescribeRule
- events:DeleteRule
- events:PutTargets
Benefits of using AWS Control Tower for integration
You can leverage the following benefits while integrating your AWS account using AWS Control Tower:
- Automatic Amazon Resource Name (ARN) role creation for multiple accounts.
- Effortlessly add multiple AWS accounts from an organization to Site24x7.
- Manage all integrated AWS accounts from a single location.
- Automatically add or remove accounts.
Integrate your AWS account with Site24x7 using AWS Control Tower
To integrate all your AWS accounts with Site24x7 using a Control Tower, follow the steps below:
- Log in to the Site24x7 web console.
- Navigate to AWS > Integrate AWS Account.
- Select Register with Control Tower.
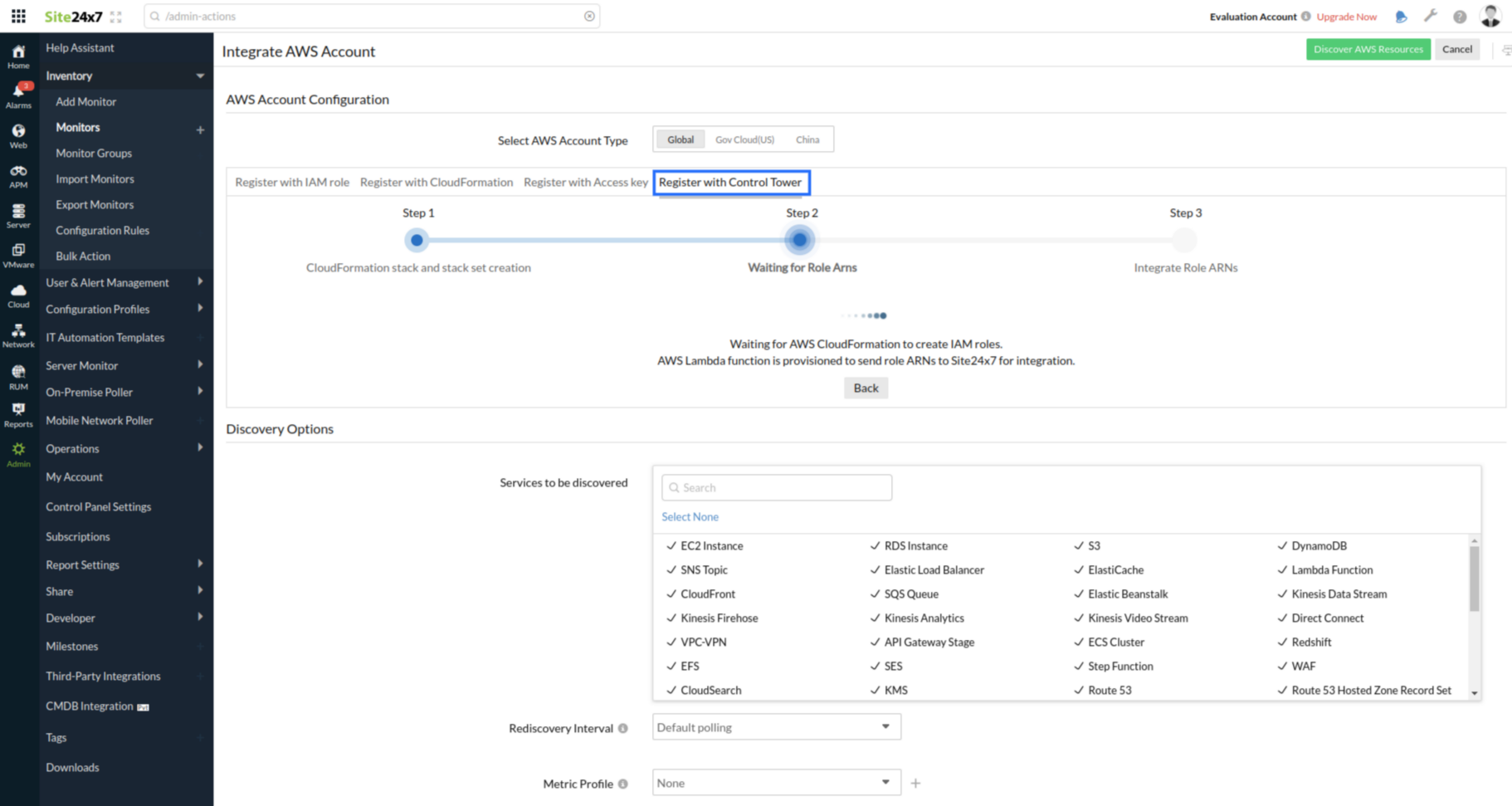
- Select the AWS region in which the CloudFormation stack needs to be created.
- Select the preferred Permissions to be attached with IAM role. Site24x7 provides two options for IAM role permissions:
- AWS Managed ReadOnlyAccess Policy: The IAM role will be created with the ReadOnlyAccess policy, which is managed by AWS for all services.
- Site24x7 Custom Policy: The IAM role will be created with the in-line policy formulated with read-only permissions required for Site24x7-supported services.
- Click Create CloudFormation Template. The CloudFormation stack in your account will automatically create all the necessary components in your account.
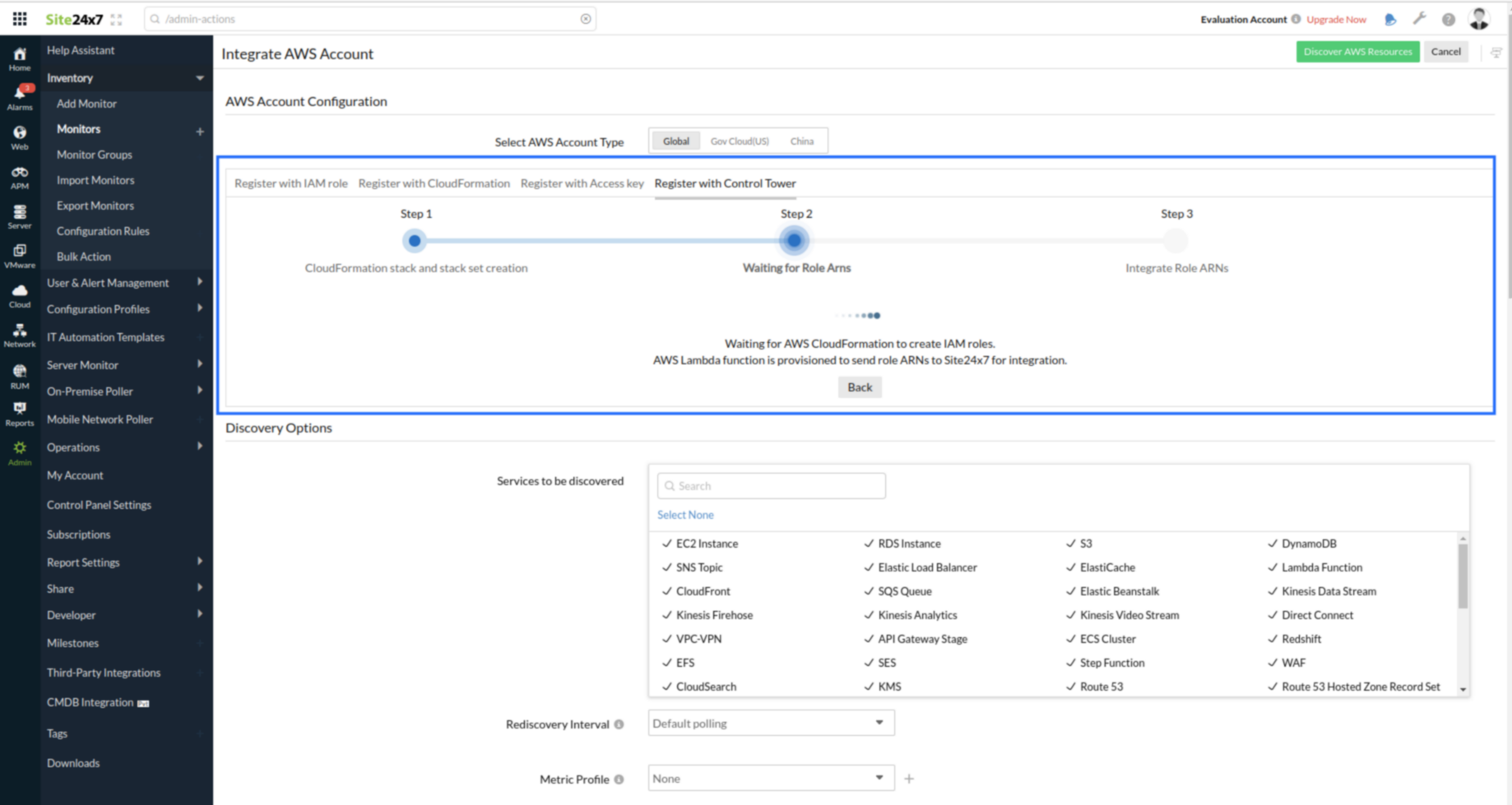
- After creating the IAM role, the CloudFormation stack and stack sets send the role ARNs to Site24x7 via the Lambda function.
- Enter the Display Name.
- Enter the RegEx (Regular Expression) to be filtered in the Accounts Filter field or select the accounts to be integrated from the Select Accounts list.
NoteIf you wish to edit the RegEx after registering with Control Tower, navigate to the Edit Integrated AWS Account page of the Control Tower and update the RegEx.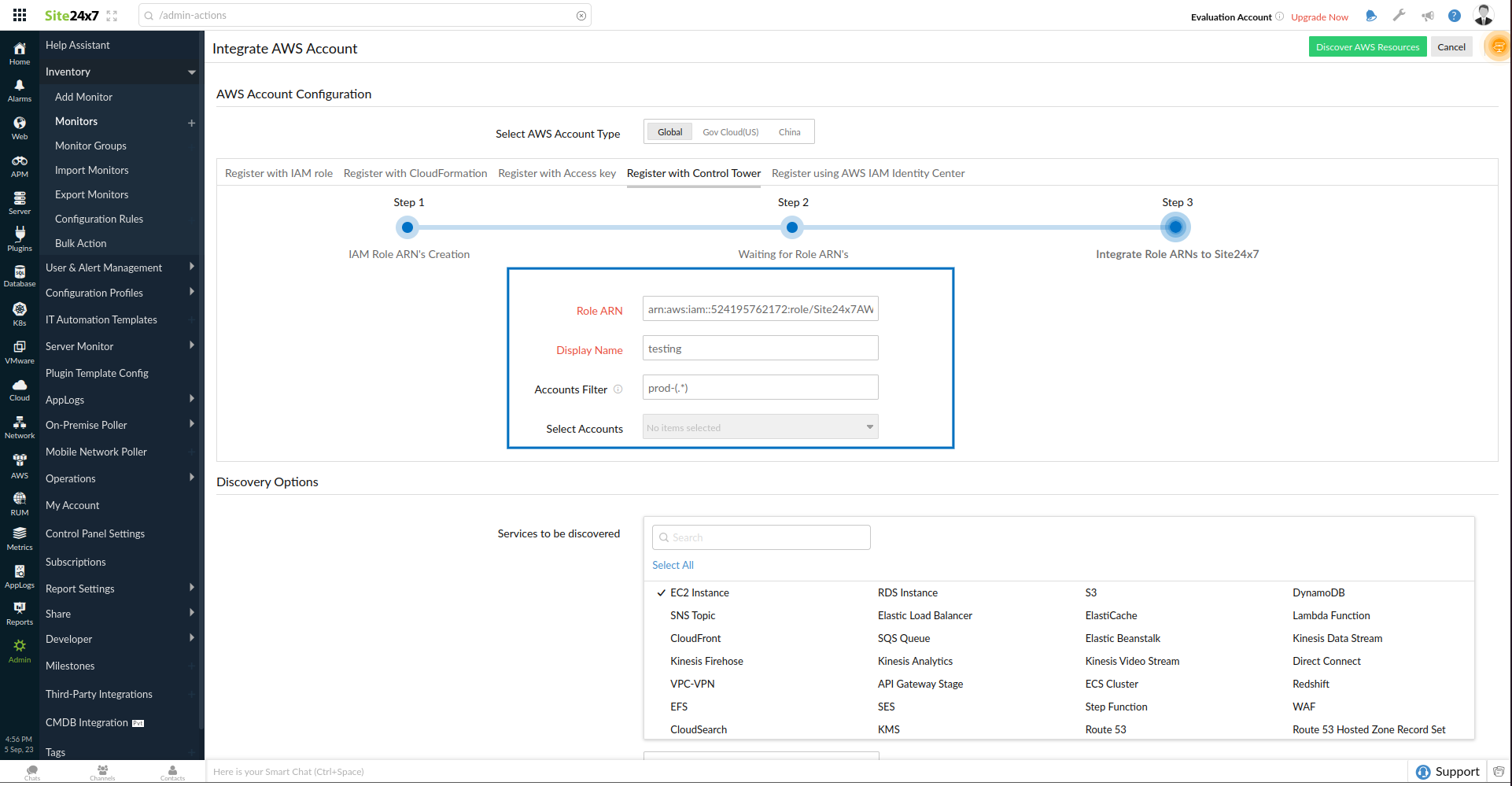
- Once the role ARNs details are fetched, you can configure settings (such as the default threshold profiles for each supported AWS service), mute resource termination alerts, and customize the Guidance Report using the Advanced Configuration option.
- Choose the services you wish to integrate with Site24x7 from the Services to be discovered list in the Discovery Options section. You can view all the integrated accounts inside the management account integrated with Site24x7.
- Click Discover AWS Resources to add the accounts.
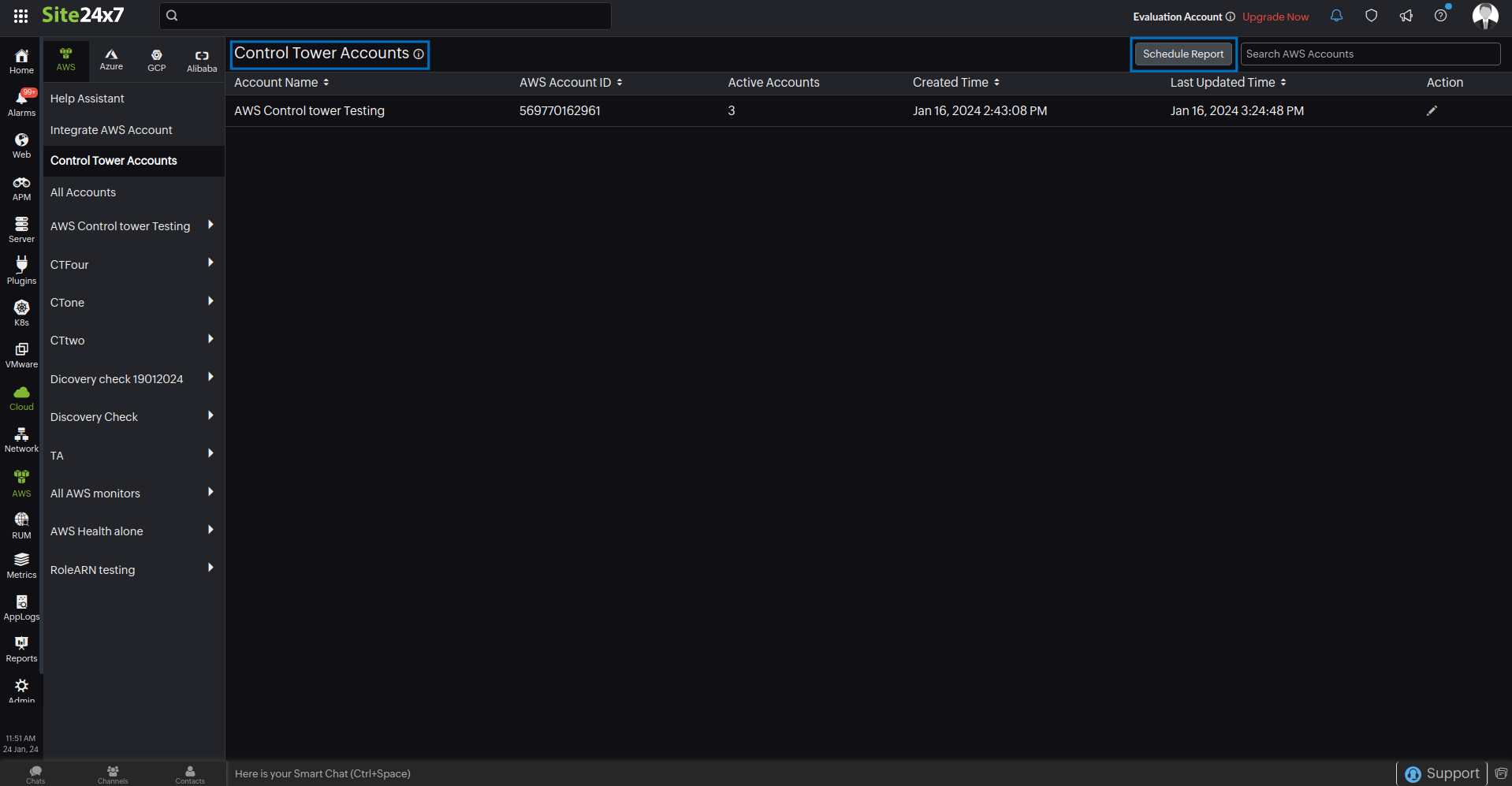
Once your AWS account is integrated with Site24x7 using AWS Control Tower, you can view all the Control Tower accounts in the Cloud > AWS > Control Tower Accounts > Control Tower Accounts page. Click Schedule Report to generate the Control Tower Accounts Report, which contains the Control Tower account details in CSV format.
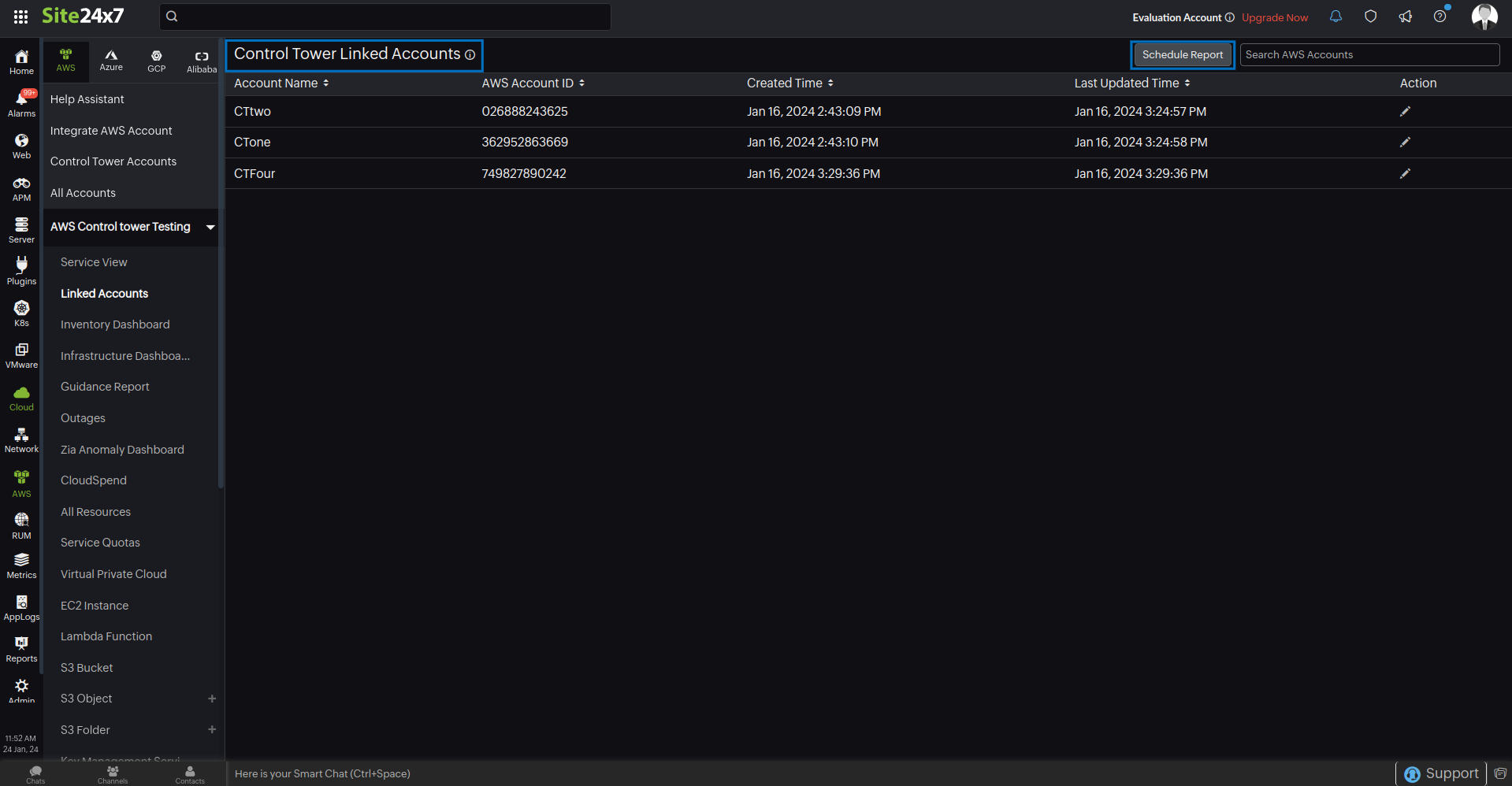
All the accounts linked to the Control Tower parent account will be listed in the Cloud > AWS > Control Tower Accounts > Control Tower Linked Accounts page. Click Schedule Report to generate the Control Tower Linked Accounts Report, which contains the Control Tower linked account details in CSV format.
- If you delete a Control Tower parent account, all the Control Tower linked accounts will also be deleted.
- If you modify the existing configuration of an AWS Control Tower parent account, then the existing changes in the Control Tower linked accounts will be overwritten as well.
- If you modify the configuration of any individual Control Tower linked account, then the changes will be reflected only for the linked account and will not affect the Control Tower parent account or any other linked accounts.
- If the Automatically Remove Closed Account option is enabled in the Integrate AWS Account > Advance Configuration section, all the closed AWS accounts will be permanently removed from Site24x7.
Updating a stack for Control Tower account
To use the latest features implemented for Control Tower accounts, you have to update the existing stacks configured for your Control Tower accounts.
To update a stack in AWS console:
- Login to AWS console.
- Navigate to All services > Management & Governance > CloudFormation.
- Select the stack that needs to be updated from the Stacks list.
- Click Update.
- Select Replace current template.
- Copy and paste the Template URL from the Site24x7's Edit Integrated AWS Account page in the Amazon S3 URL field.
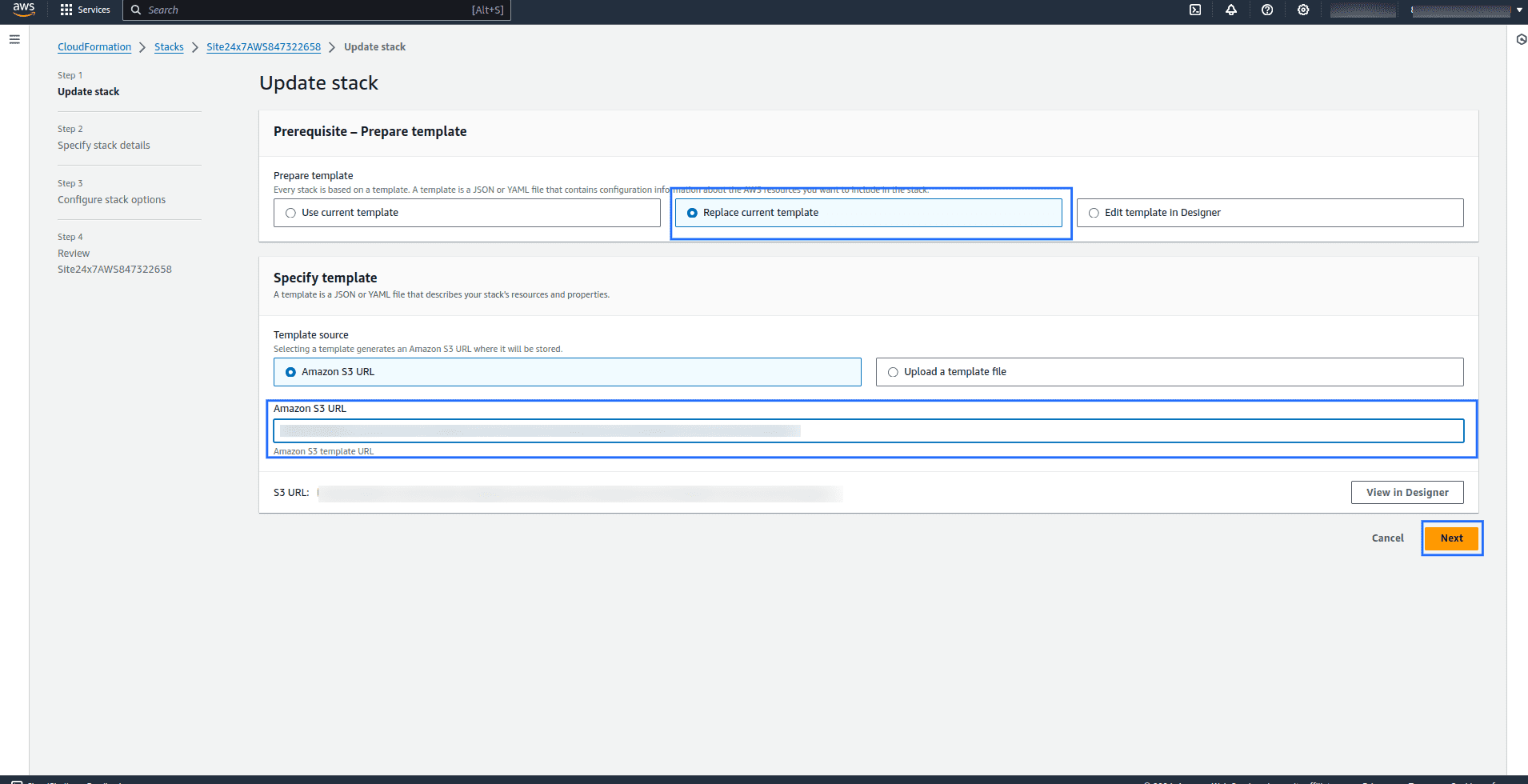
- Click Next.
- Copy and paste the Secret Rotation Key from the Site24x7's Edit Integrated AWS Account page in the APIRotateKey field.
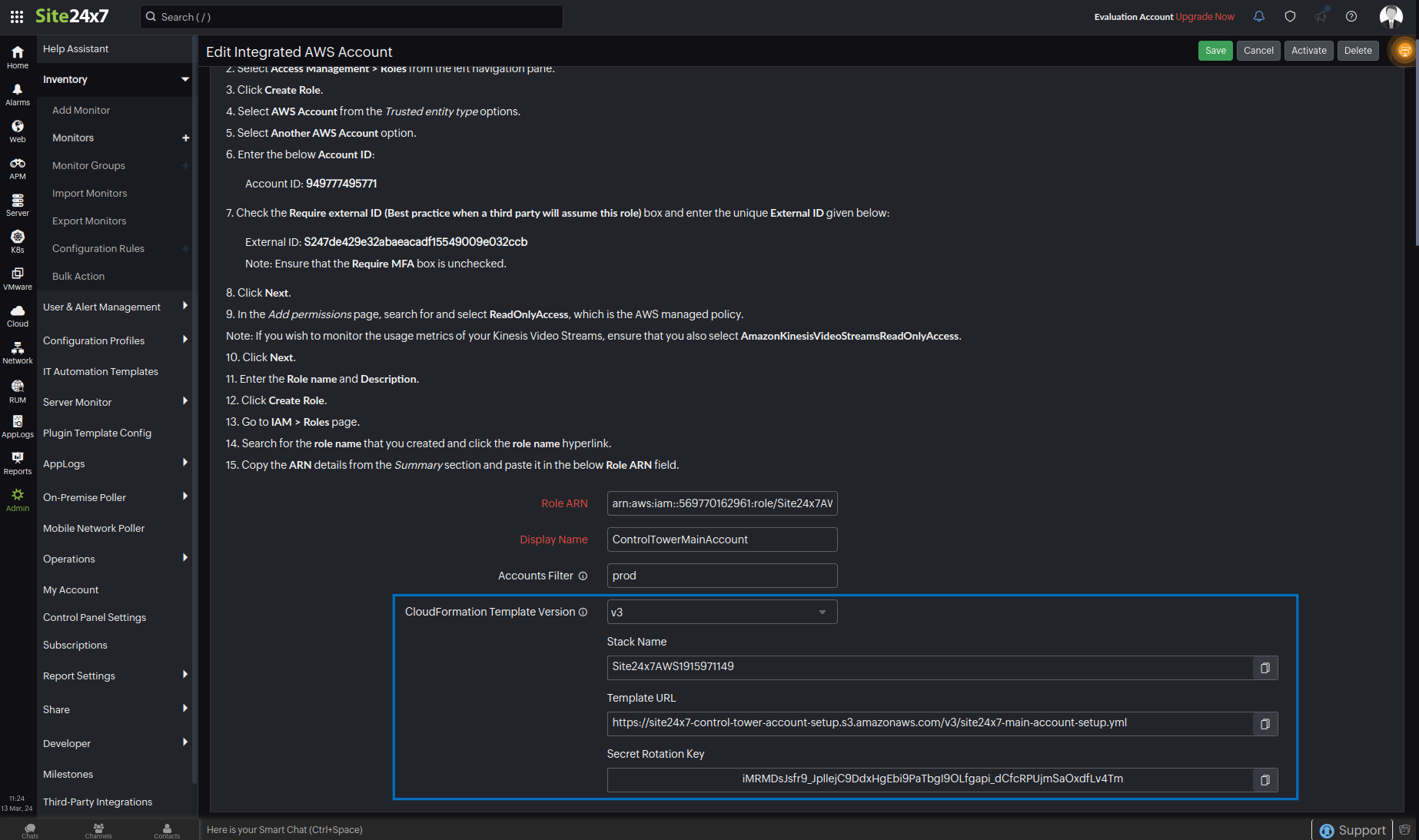 NoteThe secret rotation key feature is available only for version 3, which is the latest version. The key rotation feature enables the rotation of keys stored in the AWS Secrets Manager.
NoteThe secret rotation key feature is available only for version 3, which is the latest version. The key rotation feature enables the rotation of keys stored in the AWS Secrets Manager. - Click Next.
- Verify the details in the Configure stack options page and click Next.
- Review the stack details and select the acknowledgement check box below the Capabilities.
- Click Submit.
Once the stack update process is completed, the update status will be displayed for the selected stack in the Events tab.